How can an executable app (.exe) look like an image file?
Use the RTLO character as a trick in file extension.
RTLO stands for Right-To-Left Override. It is a Unicode non-printing character used to write languages read in the right-to-left manner. It takes the input and literally just flips the text the other way round.
RTLO Trick#
Here’s the steps to make a cmd.exe displayed as cmd_exe.jpg in Windows Explorer (with file extension being shown).
An executable file could be
.exe,.bat,.cmd,.vbs,.ps1,.com.
First, get ready with an executable file (exe).
You can convert a Python script to EXE (using PyInstaller) if you want.
Here, I’m using Windows built-in cmd.exe as my example.
- Rename the file to
cmd_gpj.exe. - Open
Character Map. - Select
Advanced view. - At the
Go to Unicodefield, type in202E. (See the bottom bar showing asU+202E: Right-To-Left Override) - Click
Copybutton. - Back to Windows Explorer to select the file
cmd_gpj.exe. - Press F2 (rename), place cursor between
cmd_andgpj.exe, press ctrl-v (paste). (The filename should be shown ascmd_exe.jpg)
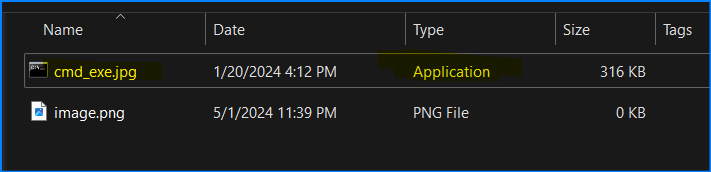
Notes:
- See the
image.pngfile has file extension being shown. - See the
cmd_exe.jpgfile has the type asApplication.
However, at the cmdline, it will look like:
C:\home\>dir
Directory of C:\home
05/01/2024 11:45 PM <DIR> .
05/01/2024 11:26 PM <DIR> ..
01/20/2024 04:12 PM 323,584 cmd_ gpj.exe
05/01/2024 11:39 PM 0 image.png
2 File(s) 323,584 bytes
But when I highlight, copy and paste the filename cmd_ gpj.exe to vim editor in Linux terminal, it will display as cmd_<202e>gpj.exe.
What’s Next?#
With the RTLO trick, we can build a trojon that looks like a image file. We need:
- An image file (.jpg).
- An executable file (.exe).
- An icon image file (.ico).
First, goto IcoConvert, and convert the image file to an icon file (.ico).
Second, use/open WinRAR:
- Select
Create SFX archive. - Click at
Advancedtab. - Click at
SFX options...button. - Click at
Setuptab. - At the
Setup programandRun after extractionsection, put in the filenames for the image file and the executable file. (This will make image file to be opened and follow by executing the executable file once the victim opens the IMAGE) - Click on the
Modetab. - Select
Unpack to temporary folderoption. - At the
Silent mode, selectHide alloption. - Click at
Text and icontab. - At the
Load SFX icon from the file, browse to previously created icon image file. - Click at
Updatetab. - At the
Overwrite mode, selectoverwrite all filesoption. - Click
OKandOK.
A new SFX (.exe) should be created now.
Next, use the RTLO trick to rename the new SFX (.exe) filename, and make it looks like a JPG file.
Here’s the simplified flow:
flowchart LR
A1(fa:fa-image image.jpg)
A2(fa:fa-gear executable.exe)
A3(fa:fa-icons cover.ico)
B1[fa:fa-screwdriver-wrench WinRAR]
C1(fa:fa-layer-group new_sfx.exe)
D1[fa:fa-gift new_sfx.jpg]
A1 --> B1
A2 --> B1
A3 --> B1
B1 -->|Generate| C1
C1 -->|RTLO| D1
